Security and compliance are shared responsibilities in the public cloud. Many organizations make the mistake of believing that because a public cloud provider manages the security and compliance of the cloud, it is also responsible for security and compliance in the cloud.
That is not the case. It is your data and, at the end of the day, if there is a breach or compliance violation, it is your company’s problem. It won’t do any good to point to a cloud provider and assign blame. It’s your revenue, reputation and customer relationships that are at stake, not the provider's.
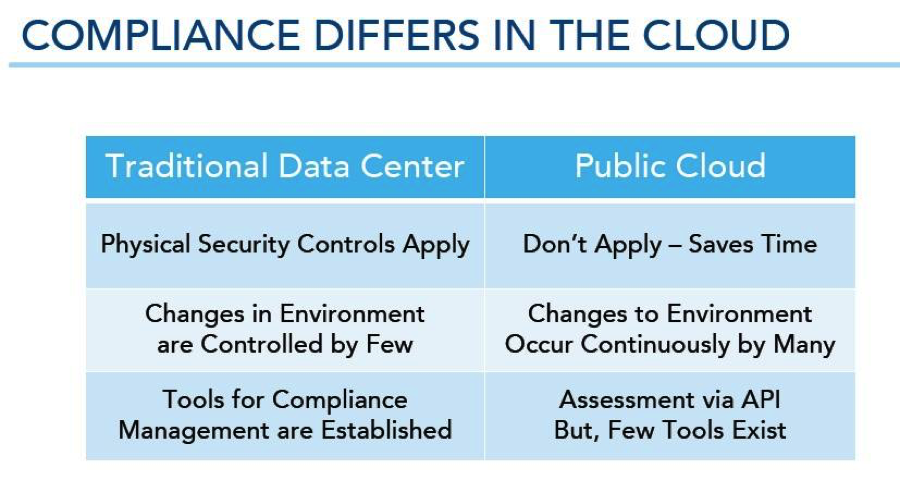
Therefore, CIOs and CISOs must adapt their traditional security and compliance processes to address what’s different in the cloud. The following table illustrates key points of differentiation in managing compliance in traditional data centers versus public clouds.
What is a security-first model for compliance?
IT and security leaders in companies of all sizes across all industries have discovered that by taking a security-first approach in the cloud, they can achieve a state of state of continuous compliance, thereby lowering costs, minimizing risk and reducing complexity.
Cloud environments can change very quickly, which means they are usually in constant flux, moving in and out of compliance. The security-first model focuses on continuous monitoring and management of cloud security risks and threats, leveraging modern tools and automation techniques to ensure that, at all times, the organization is:
- Monitoring security threats through real-time discovery.
- Understanding these threats through deep insights.
- Acting on threats through automated policies, processes and controls.
- Measuring security and compliance results through robust reporting capabilities.
Achieving this state of continuous security-first compliance requires the use of modern tools and a cloud-native security platform that leverages the API-centric architecture of the public cloud.
Benefits of the security-first model
By using a platform that allows the continuous monitoring and management of security in the cloud against policy, IT and security teams will have greater assurance that the organization will be compliant within the required frameworks. Benefits of this model are:
- Compiling a complete unified view across all cloud accounts.
- Generating compliance reports without the need for specialized knowledge.
- Identifying, prioritizing and remediating compliance risks as they arise.
- Monitoring compliance throughout the entire development lifecycle.
- Avoiding events that disrupt DevOps teams with last-minute fire drills to meet compliance requirements.
- Demonstrating to auditors that the organization is managing security 24/7/365—not just in the last few weeks before the audit.
Continuous compliance automation also helps those in the organization who are responsible for compliance and DevOps. Compliance can respond faster to third-party security audits, thus making security a competitive differentiator. Development teams don’t get bogged down once a year to stop projects for compliance audits.
Conclusion
Managing compliance in the cloud is a lot different than managing it on premises. In the cloud, there are points at which IT loses visibility and control. In addition, the environment is constantly in flux, with a wide range of individuals capable of making changes at any time. It can be exceedingly complex, and even the most expert teams can have problems if they don’t have the right solutions in place.
Fortunately, there are modern security platforms that have been designed specifically to meet the challenges of public cloud environments. With a modern approach, organizations can take advantage of a security-first model that enables continuous visibility through automation. This will not only strengthen security, it will provide compliance and DevOps teams with the tools and processes they need to successfully meet the requirements of the cloud era.

