Amazon RDS (Relational Database Service)
What is Amazon RDS (Relational Database Service)?
Amazon Relational Database Service (RDS) is a managed database service provided by Amazon Web Services (AWS). It makes it easy to set up and operate a scalable relational database in the AWS cloud. Amazon RDS supports an array of database engines to store and organize data. It also takes care of many database management and administration tasks, such as data migration, backup, recovery and patching, freeing up administrators to focus on other higher value tasks.
Amazon RDS facilitates the deployment and maintenance of relational databases in the AWS cloud. It can be used to set up, operate, manage and scale a relational instance of a cloud database. The basic building block of Amazon RDS is a database instance, which can contain one or more databases and can be accessed with the same tools and applications used with any standalone database instance.
Amazon RDS is not itself a database; it is a service -- in fact, a collection of services -- to manage relational databases. These services make it easy to deploy relational database engines either on premises (using AWS Outposts) or with elevated access to the database environment and its underlying operating system (using Amazon RDS Custom).
A database engine is a specific relational database software that runs on the organization's database instance. Amazon RDS supports eight engines:
- Amazon Aurora PostgreSQL-Compatible Edition.
- Amazon Aurora MySQL-Compatible Edition.
- RDS for PostgreSQL.
- RDS for MySQL.
- RDS for MariaDB.
- RDS for SQL Server.
- RDS for Oracle.
- RDS for Db2.
AWS provides other database services, including the following:
- Amazon DynamoDB key-value and document database for NoSQL databases.
- Amazon Neptune for graph databases.
- AWS Database Migration Service to ease database transfers and transformations.
How does Amazon RDS work?
Amazon RDS is available for three different deployment environments: Amazon RDS, Amazon RDS Custom and Amazon RDS on AWS Outposts.
Amazon RDS allows organizations to deploy a relational database in the cloud and connect their app to one of seven Amazon RDS engines. The offering includes multiple managed features for:
- Security and compliance.
- Data durability and redundancy.
- Performance.
- Scalability.
- Patching and upgrades (automated).
- Monitoring (includes alerting).
- Data/workload backup and recovery.
Amazon RDS Custom allows organizations to connect to the Amazon RDS endpoint with privileged access. This managed database service -- available for Oracle and SQL Server -- is ideal for applications that require database and operating system customization, and for legacy, custom and packaged applications. With Amazon RDS Custom, all AWS resources are deployed into the organization's AWS account. A support perimeter monitors the environment and raises alerts if it detects invalid customizations.
Amazon RDS on AWS Outposts supports hybrid workloads and allows for the deployment of on-premises Amazon RDS managed databases. AWS Outposts is a fully managed service that provides resizable and cost-effective capacity for on-premises databases and automates time-consuming administration tasks. AWS securely deploys Amazon RDS to the organization's data center which the organization can then manage using their current AWS Management Console, CLI, and application programming interfaces. The databases are encrypted (using Amazon KMS) and backups are stored automatically (locally or in the AWS Region).
Amazon RDS features
Amazon RDS features include the following:
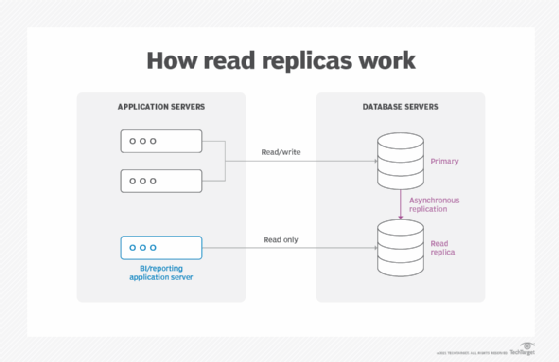
Replication. Read replicas help to increase read scaling and throughput for read-heavy database workloads. These are read-only copies of database instances that applications use without altering the original production database. Administrators can also enable automatic failover across multiple availability zones through RDS Multi-AZ deployment and with synchronous data replication.
Integration. The integration with AWS CloudFormation makes it easy for users to model, provision and manage AWS resources across AWS accounts and Regions.
Database metrics. Users can view database metrics, such as compute/memory/storage capacity utilization, input/output (I/O) activity, and instance connections through the Amazon RDS Console. They can also detect performance problems through the Amazon RDS Performance Insights tool.
Support for blue/green deployments. These deployments create a staging environment that mirrors the production environment and allow users to make quick database updates without data losses.
Multiple storage options. RDS provides price flexibility with three types of storage: general-purpose solid-state drive (SSD), provisioned I/O operations per second and magnetic.
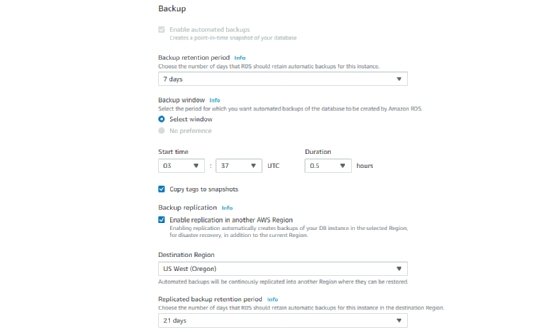
Patching and backups. Automated patching helps maintain the database's high performance, reliability and security, while automated backups enable point-in-time recovery for database instances. Users pick a retention period and restore databases to any time during that period. They also can manually take snapshots of instances that remain until they are manually deleted.
Incremental billing. Users pay only a monthly fee for launched instances.
Security. Both data at rest and data in transit are encrypted. RDS uses Amazon KMS to manage the encryption keys for the relational database. Additionally, the Secure Sockets Layer protocol can be used to secure and protect data in transit.
What are the advantages of Amazon RDS?
As a managed database service, Amazon RDS minimizes the complexity associated with managing large relational databases. Additionally, Amazon RDS frees up database administrators from many tedious and time-consuming database administration tasks, including the following:
- Infrastructure provisioning.
- Software maintenance.
- Patching.
- Backup.
- Recovery.
- Failure detection.
- Repair.
Other benefits of Amazon RDS include the following:
- Ease of use. Admins don't need to learn specific database management tools and can manage multiple database instances using the management console.
- Familiarity and choice. RDS is compatible with many database engines that many users are already familiar with. These engines can be deployed in the cloud or on premises as required.
- Cost-effectiveness. RDS customers only pay for what they use, providing a cost-effective way to deploy, use and benefit from relational databases in the cloud.
- High availability. High availability is ensured with multi-AZ deployments, primary instances and synchronous secondary instances.
- Reliable backup and restore. Amazon RDS manages backups which can be turned on automatically and used to restore a database reliably and efficiently.
- High security. RDS customers can define users and permission with AWS Identity and Access Management to control dataset access. The database can also be placed in a virtual private cloud to protect it from unauthorized access and compromise.
What are the drawbacks of Amazon RDS?
Some downsides of using Amazon RDS include the following:
- Lack of root access. Because it is a managed service, users do not have root access to the server running RDS. RDS restricts access for certain procedures to those with advanced privileges.
- Downtime. Systems must go offline for some patching and scaling procedures. The timing on these processes varies. With scaling, compute resources need a few minutes of downtime on average.
Amazon RDS database instances
A database administrator can create, configure, manage and delete an Amazon RDS instance, along with the resources it uses. An Amazon RDS instance is a cloud database environment. Admins can also spin up many databases or schemas; how many depends on the database used.
Amazon RDS limits each customer to a total of 40 database instances per account. AWS imposes further limitations for Oracle and SQL Server instances. With those database instances, a user generally can only have up to 10.
Amazon RDS use cases
Amazon RDS' scalability, security and availability make it useful for a variety of applications. Some possible uses include the following:
- Online retailing. These applications manage complex databases that track inventories, transactions and pricing.
- Mobile and online gaming. RDS supports developers who need to continuously update these applications and users who need high availability.
- Travel applications. Applications like Airbnb take advantage of RDS' ability to simplify time-consuming database administration tasks and automate database replication. Mobile apps like Airbnb also take advantage of RDS' scalable storage capability.
- Streaming applications. Applications like Netflix take advantage of Amazon RDS' storage scalability as well as availability, which allows them to handle high demand daily.
- Finance applications. These applications, like other mobile applications, can use RDS to simplify administrative database tasks and save time and money.
Business-to-business reporting company Enlyft said 6,096 companies were using Amazon RDS in 2021, including The American Red Cross, Penguin Random House and Zendesk. Amazon also reported in 2021 that Airbnb, Intuit and the U.S. Department of Veterans Affairs are among the organizations that use RDS to support their data workloads.
Amazon Aurora and Amazon Aurora Serverless vs. Amazon RDS
Amazon Aurora is a database engine created by Amazon. RDS is a service used to manage database engines and instances, including Amazon Aurora databases.
Amazon Aurora Serverless can also be used to manage instances of Amazon Aurora. Its automation features relieve developers from having to manually launch servers and manage database capacity.
With RDS, servers must be manually scaled, which can result in significant downtime. Aurora Serverless' automatic scaling capability enables faster deployment with little to no downtime.
One downside of Aurora Serverless is it only works with Amazon Aurora, MySQL and PostgreSQL. RDS is compatible with six database engines.
Organizations should assess the two database management options. Both have advantages and limitations, depending on the type of application they serve. Aurora Serverless is considered suitable for applications with unpredictable and steep spikes in usage, which need more efficient capacity adjustments. Amazon RDS is suitable for more predictable applications because capacity adjustments take more time in RDS than in Aurora Serverless.
The takeaway
Amazon RDS helps organizations handle relational database management tasks such as migration, backup, recovery and patching. Some of the main features of Amazon RDS are replication, high performance storage and failure detection.
One of the biggest advantages of Amazon RDS is its ease of use. It lets administrators manage multiple database instances without having to learn other database management tools.
These features enable RDS to help organizations cut costs that come from time-consuming database administration tasks and manage the hidden costs that come with using high-performance storage in AWS.
It is important to take steps to avoid excessive charges and keep cloud costs under control. Learn more about ways to manage AWS costs.





