Amazon Elastic Compute Cloud (EC2)
What is Amazon Elastic Compute Cloud (EC2)?
Amazon Elastic Compute Cloud (EC2) is a web-based service that enables businesses to run application programs in the Amazon Web Services (AWS) public cloud. With Amazon EC2, companies can access scalable and secure computing capacity on demand to run many kinds of workloads in AWS.
Amazon EC2 is a cloud-based platform that provides on-demand, scalable computing capacity for many kinds of enterprise applications and workloads.
Through Amazon EC2, teams can access reliable, scalable infrastructure and secure computing capabilities in the AWS cloud to develop applications without having to invest in expensive on-premises hardware.
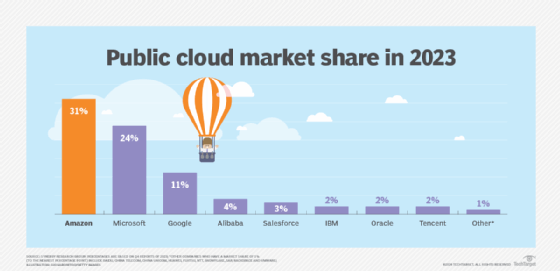
It's easy to add or reduce capacity based on changing business requirements and control AWS costs based on capacity used. The AWS cloud consists of more than 200 individual services, and as shown here, AWS is one of the largest cloud providers.
The Amazon EC2 platform includes more than 750 instances (virtual servers) of different types to support different types of enterprise workloads. Users can also choose from the latest processor, storage, networking, operating system and purchase model to meet their requirements. These components are packaged into pre-configured templates for every Amazon EC2 instance.
Key use cases for Amazon EC2
Amazon EC2 is a good computing platform for running cloud-native and enterprise applications. It can help organizations looking to launch virtual servers, configure security and networking, and manage storage in the cloud. Its ability to provide on-demand, scalable infrastructure and capacity, plus a wide range of instance types, also makes it highly suitable for all these use cases:
- Web servers.
- Code repositories.
- Batch processing.
- Media transcoding.
- High-performance web servers.
- High-performance computing (HPC).
- Scientific modeling.
- Dedicated gaming servers.
- Processing of large memory data sets.
- Ad server engines.
- Input/output (I/O)-intensive applications.
- Computational fluid dynamics.
- Weather forecasting.
- Molecular dynamics.
Amazon EC2 is also optimized for machine learning inference, deep learning and generative artificial intelligence applications. Users can also use Amazon EC2 to build on-demand macOS workloads for Apple devices and platforms.
Amazon EC2 instance types
An Amazon EC2 instance is a virtual server offering an appropriate mix of resources used to run applications on the AWS infrastructure without having to purchase any hardware. These instances, which differ in terms of the central processing unit (CPU), memory, storage and networking capacity offered, include the following:
- General purpose. These instances can be used for many different workloads, especially workloads that depend upon a balance of compute, memory and networking resources.
- Compute-optimized. These instances are meant for compute-bound or compute-intensive applications, such as batch processing, media transcoding and HPC.
- Memory-optimized. This set of instances delivers fast performance for workloads that process large memory data sets.
- Accelerated computing. These instances use hardware accelerators to perform certain functions more efficiently compared to CPU software.
- Storage-optimized. These instances deliver a high amount of low-latency, random I/O operations per second (IOPS) for workloads that require high sequential read/write access to large local data sets.
- HPC-optimized. These instances offer the best price performance for running HPC workloads at scale on AWS, such as complex simulations and deep learning workloads.
Regardless of which instance users select, Amazon EC2 enables them to scale their resources to match the requirements of their target workloads. It's also possible to choose between Fixed Performance instance families and Burstable Performance instance families, with the latter providing a baseline level of CPU performance, plus the ability to burst above the baseline.
Amazon EC2's Elastic Block Store-optimized instances deliver dedicated throughput between Amazon EC2 and Amazon EBS, which minimizes contention between Amazon EBS I/O and other traffic from the EC2 instance and provides optimal performance for EBS volumes. For an additional fee, some Amazon EC2 instance types can run as an EBS-optimized instance.
How Amazon EC2 works
To begin using Amazon EC2, users sign up for a root account on AWS. They can then use AWS Management Console to manage Amazon EC2.
Next, they identify the instance type that's most suitable for their workload. They then create a virtual machine (VM) by selecting Launch Instance in the Amazon EC2 dashboard. Once the instance is launched, it's easy to connect to it. The easiest way to connect to the instance, if it has a public IPv4 address, is with EC2 Instance Connect, a browser-based client, via this simple four-step process:
- In the Amazon EC2 console navigation pane, choose Instances.
- Select the EC2 instance -- where the connection is required -- and choose Connect.
- Select EC2 Instance Connect.
- Verify the username, and choose Connect.
If a new terminal window opens, it means the user is connected to that instance.
It's also possible to connect to an Amazon EC2 instance via the following:
- Use a Secure Socket Shell key and then connect to the instance from a preferred SSH client while using the EC2 Instance Connect application programming interface.
- Configure AWS Command Line Interface, and use the instance ID and an SSH client to connect to the instance via Amazon EC2 Instance Connect.
Important features of Amazon EC2
Some of the important features of Amazon EC2 are the following:
- Multiple storage options. Users can choose between multiple storage options, including block-level storage, instance storage and object storage for their specific requirements. Additionally, Amazon EBS provides persistent storage volumes and three volume types -- General Purpose, Provisioned IOPS and Magnetic -- depending on the workload type and need.
- Enhanced Networking. This provides high packet-per-second performance, low network jitter and low latency compared to traditional implementations.
- Access to Intel's features. Amazon EC2 instances that feature an Intel processor lets users access many processor features, including Intel Advanced Encryption Standard New Instructions, Intel Advanced Vector Extensions, Intel Deep Learning Boost and Intel Turbo Boost Technology.
- Support for cluster networking. Some Amazon EC2 instances support cluster networking when launched into a common cluster placement group for low-latency networking between the instances in the cluster.
- Auto Scaling. Users can automatically scale Amazon EC2 capacity up or down by adding or removing instances according to their own conditions, using EC2's dynamic and predictive scaling policies.
- Optimized CPU configurations. With this feature, users can better control their Amazon EC2 instances by specifying a custom number of virtual CPUs when launching new instances. They can also disable Intel Hyper-Threading Technology for workloads that perform well enough with single-threaded CPUs.
Amazon EC2 users can also benefit from these features:
- AWS Regions and Availability Zones (AZs) to improve availability and reduce latency.
- Access to Amazon Time Sync Service, a highly accurate, reliable and available time source.
- Amazon EC2 Fleet to optimize scale, performance and cost.
- Elastic Fabric Adapter to run applications requiring high levels of interinstance communications at scale on AWS.
- AWS PrivateLink to access Amazon services in a highly performing, highly available manner.
- Regular maintenance performed by AWS with minimal disruptions across instances.
Amazon EC2 pricing
Like all other AWS services, Amazon EC2 is available on a pay-as-you-use basis. Users are billed for per-second use and pay only for what they use.
The cost of instances depends on their type: On-Demand, Reserved or Spot.
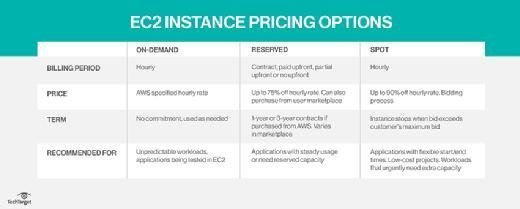
On-Demand Instances enable organizations to access computing capacity as needed and pay for it by the hour or second. There are no long-term commitments.
Reserved Instances (RIs) provide a price discount of up to 72% (discounted hourly rate) in exchange for one- or three-year contract commitments. Organizations can use these instances to reserve capacity in a specific AZ. Three types of RIs are available: Standard, Convertible and Scheduled. Standard and Convertible RIs are suitable for steady-state usage, and Scheduled RIs are suitable for matching capacity reservation to a predictable recurring schedule.
Amazon EC2 Spot Instances are available at up to a 90% discount compared to On-Demand Instances. Spot Instances can be combined with RIs and On-Demand Instances to optimize cost and performance. On their own, Spot Instances are suitable for running several workload types: containerized, big data, machine learning, HPC and continuous integration/continuous delivery pipelines.
Apart from these instance types, Amazon EC2 customers can also adopt a flexible EC2 Instance Savings Plan to save up to 72% compared to On-Demand Instances. The plan automatically applies to eligible AWS usage but requires a one- or three-year hourly spend commitment.
Amazon EC2 benefits
It's easy to get started with Amazon EC2 and access on-demand computing capacity as required. After the instance has been launched, users can connect to it. They can use EC2 Instance Connect, for example, and employ it as easily as a computer that's sitting in front of them.
Amazon EC2 offers multiple instance types and offers a wide range of computing, memory and networking resources, making it a suitable solution for many kinds of enterprise workloads. The instances are secured using numerous controls to support all applications. One such control is a security group -- a virtual firewall that controls incoming and outgoing traffic. In addition, both private and public keys are used to authorize users and prevent unauthorized access.
Amazon EC2 supports dynamic cloud computing with elastic IP addresses. These addresses are static IPv4 addresses, with each address associated with the user's account rather than a particular instance. Also, users can control the address until they explicitly release it or choose not to do so.
Users can create Virtual Private Clouds to launch Amazon EC2 resources in a virtual network. This network is user-defined and logically isolated from the rest of the AWS cloud. It uses AWS' scalable infrastructure and can be connected to the user's own network.
Another benefit of Amazon EC2 is that it offers a free tier. With this tier, users can familiarize themselves with some of its features and pay only when they are ready for the full offering. The free version includes 750 hours of Linux and Windows t2.micro instances per month for a year.
Challenges with Amazon EC2
Amazon EC2 does have some implementation challenges:
- Resource utilization. Developers must manage the number of instances to avoid costly large, long-running instances.
- Security. Developers must ensure that public-facing instances are running securely.
- Deploying at scale. Running a multitude of instances can result in cluttered environments that are difficult to manage.
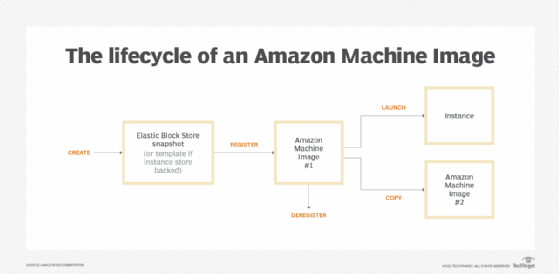
- Management of Amazon Machine Image (AMI) lifecycle. Developers often begin by using default AMIs. As computing needs change, custom configurations will likely be required.
![A chart showing the Amazon Machine Image lifecycle]()
Steps in the lifecycle of an Amazon Machine Image - Ongoing maintenance. Amazon EC2 instances are VMs that run in Amazon's cloud. However, they ultimately run on physical hardware, which can fail. AWS alerts developers when an instance must be moved due to hardware maintenance. This requires ongoing monitoring.
Amazon EC2 history
Amazon EC2 was the idea of engineer Chris Pinkham, who conceived it as a way to scale Amazon's internal infrastructure and build an "infrastructure service for the world." Pinkham and fellow engineer Benjamin Black presented their ideas to Amazon CEO Jeff Bezos, who then requested more details about virtual servers in the cloud.
Amazon EC2 was then developed by a team in Cape Town, South Africa. Pinkham provided the initial architecture guidance, gathered a development team and worked on the project along with Black and Willem van Biljon.
In 2006, Amazon announced a limited public beta test of Amazon EC2, and in 2007, the company added two new instance types: Large and Extra-Large. Amazon announced the addition of static IP addresses, AZs and user-selectable kernels in spring 2008, followed by the release of EBS in August 2008.
Amazon EC2 went into full production on Oct. 23, 2008. Amazon also released a service-level agreement for Amazon EC2 that day, along with Microsoft Windows and SQL Server in beta form on Amazon EC2. Amazon added AWS Management Console, load balancing, autoscaling and cloud monitoring services in 2009.
Today, Amazon EC2 is among the most popular of AWS' products and remains one of the foundational elements of Amazon's cloud computing service.
Amazon EC2 vs. Amazon S3
Amazon EC2 and Amazon Simple Storage Service (S3) are important services that help developers maximize the use and benefits of the AWS cloud.
The main difference between the services is that Amazon EC2 is a computing service that enables companies to run servers in the cloud and access computing capacity for different types of workloads, whereas Amazon S3 is an object storage service used to store and retrieve data from AWS through the internet. Amazon S3 is like a giant hard drive in the cloud, while Amazon EC2 offers computing resources like CPU and RAM beside storage.
Many users and organizations use both services for their cloud computing needs. With Amazon S3, users can store files and data sets that are used with Amazon EC2 instances. The data can be stored and retrieved for many kinds of use cases, including data lakes, websites, backups and big data analytics.
Amazon EC2 and AWS Lambda meet different needs in an AWS cloud environment. They can also work together, however. Check out our overview of Amazon EC2 vs. AWS Lambda.