Amazon EC2 instance
What is an Amazon EC2 instance?
An Amazon EC2 instance is a virtual server in Amazon's Elastic Compute Cloud (EC2) for running applications on the Amazon Web Services (AWS) infrastructure. AWS is a comprehensive, evolving cloud computing platform; EC2 is a service that enables business subscribers to run application programs in the computing environment. It can serve as a practically unlimited set of virtual machines (VMs).
Amazon provides various types of instances with different configurations of CPU, memory, storage and networking resources to suit user needs. Each type is available in various sizes to address specific workload requirements.
Instances are created from Amazon Machine Images (AMI). The machine images are like templates. They are configured with an operating system (OS) and other software, which determine the user's operating environment. Users can select an AMI provided by AWS, the user community or through the AWS Marketplace. Users also can create their own AMIs and share them.
EC2 instance types
Instance types are grouped into families based on target application profiles. These groups include the following:
- General purpose. A general purpose instance is a VM that is designed to handle a variety of workloads. General purpose instances are optimized to have a high number of CPU cores, on-demand storage and memory. Some common use cases for general purpose instances include web server hosting and software development and testing.
- Compute optimized. Compute optimized instances are used to run big data applications that require large amounts of processing power and memory on the AWS cloud. These instances are designed and optimized for running computational and data-intensive applications that require fast network performance, extensive availability and high input/output (I/O) operations per second (IOPS). Examples of types of applications includes scientific and financial modeling and simulation, machine learning, enterprise data warehousing and business intelligence.
- Graphics processing unit (GPU). These instances provide a way to run graphics-intensive applications faster than with the standard EC2 instances. Systems that rely on GPUs include gaming and design work. For example, Linux distributions often take advantage of GPUs for rendering graphical user interfaces, improving compression speeds and speeding up database queries.
- Memory optimized. Memory optimized instances use a high-speed, solid-state drive to provide ultra-fast access to data and deliver high performance. These instances are ideal for applications that require more memory and less CPU power, including open source databases, real-time big data analytics and in-memory caches.
- Storage optimized. Storage optimized instances are ideal for applications that require high I/O performance, such as NoSQL databases that store and retrieve data in real time. They're also well suited for memory-intensive applications such as data processing, data warehousing, analytics workloads and log processing.
- Micro. A micro instance is meant for applications with low throughput. The micro instance type can serve as a small database server, as a platform for software testing or as a web server that does not require high transaction rates.
Amazon EC2 instance features
Many EC2 instance features are customizable, including the storage, number of virtual processors and memory available to the instance, OS and the AMI on which the instance is based. The following are Amazon EC2 instance features:
- Operating system. EC2 supports many OSes, including Linux, Microsoft Windows Server, CentOS and Debian.
- Persistent storage. Amazon's Elastic Block Storage (EBS) service enables block-level storage volumes to be attached to EC2 instances and be used as hard drives. With EBS, it is possible to increase or decrease the amount of storage available to an EC2 instance and attach EBS volumes to more than one instance at the same time.
- Elastic IP addresses. Amazon's Elastic IP service lets IP addresses be associated with an instance. Elastic IP addresses can be moved from instance to instance without requiring a network administrator's help. This makes them ideal for use in failover clusters, for load balancing, or for other purposes where there are multiple servers running the same service.
- Amazon CloudWatch. This web service allows for the monitoring of AWS cloud services and the applications deployed on AWS. CloudWatch can be used to collect, store and analyze historical and real-time performance data. It can also proactively monitor applications, improve resource use, optimize costs and scale up or down based on changing workloads.
- Automated scaling. Amazon EC2 Auto Scaling automatically adds or removes capacity from Amazon EC2 virtual servers in response to application demand. Auto Scaling provides more capacity to handle temporary increases in traffic during a product launch or to increase or decrease capacity based on whether use is above or below certain thresholds.
- Bare-metal instances. These virtual server instances consist of the hardware resources, such as a processor, storage and network. They are not virtualized and do not run an OS, reducing their memory footprint, providing extra security and increasing their processing power.
- Amazon EC2 Fleet. This service enables the deployment and management of instances as a single virtual server. The Fleet service makes it possible to launch, stop and terminate EC2 instances across EC2 instance types with one action. Amazon EC2 Fleet also provides programmatic access to fleet operations using an API. Fleet management can be integrated into existing management tools. With EC2 Fleet, policies can be scaled to automatically adjust the size of a fleet to match the workload.
- Pause and resume instances. EC2 instances can be paused and resumed from the same state later on. For example, if an application uses too many resources, it can be paused without incurring charges for instance usage.
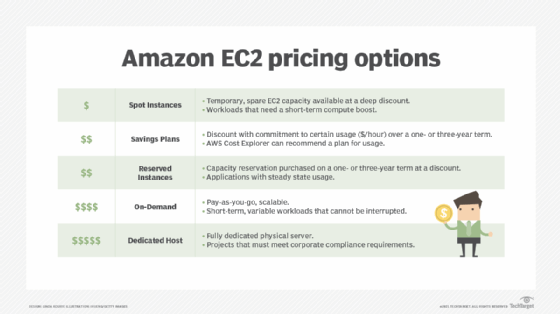
The cloud cost model can be challenging. Find out the steps to take to effectively manage AWS costs, including EC2 instances; identify ways to save; and keep your cloud costs in check.






