
cutimage - Fotolia
12 AWS security tools to protect your environment and accounts
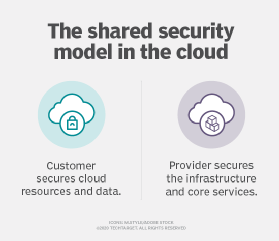
AWS manages the security of the cloud, but it's your job to secure your data in the cloud.
As the shared responsibility model outlines, cloud users are responsible for securing their data, applications and networks in the cloud.
In this article, we'll review the basic AWS security tools to handle infrastructure protection, identity and access management, threat detection and data protection. Unless otherwise indicated, you can use these AWS security tools for free as part of your account. However, the resources they consume will show up in your bill.
Identity and access management
AWS Identity and Access Management (IAM). This is Amazon's core service for controlling access to your AWS resources. With AWS IAM, you create user accounts or specific AWS roles, and then establish permissions that define which resources they can access. You can set these permissions on an individual account or group basis. You can also add extra identity protections, such access keys or a multifactor authentication device.
AWS Single Sign-On (SSO). With AWS SSO, you can link your AWS account to your existing credentials for business applications, such as Salesforce and Office 365. It works with in-house, custom applications as well. You can access all your applications, AWS and otherwise, through your personal SSO portal.
AWS Directory Service for Microsoft Active Directory. This managed service syncs Microsoft Active Directory with the AWS cloud. When set up, users and groups can access resources from their managed directories in AWS and on premises. The service supports single sign-on across AWS and Microsoft applications and services. It also provides secure connections between Linux and Windows instances on AWS.
AWS Resource Access Manager (RAM). With this service, you can share access to cloud resources with other AWS accounts operating within your company. You create a resource share and attach one or more resources to it. Then, you identify the AWS account or Organization that can share those assets. You won't be charged for sharing a resource, but that resource will become more expensive if more accounts are using it.
Amazon Cognito. This service provides authentication and access management for web and mobile apps built on AWS. Your users can sign in directly with Cognito or third-party identity providers like Google or Facebook. Cognito has two main features -- user pools and identity pools -- that you can use together or separately. A user pool is a directory where your app users can sign in or sign up. Identity pools are federated identities created to give users limited access to other Amazon cloud services. Billing is based on monthly active users.
Threat detection
Amazon GuardDuty. This monitoring service uses machine learning to look for malicious activity within an AWS environment. This activity could be contact with questionable IP addresses, exposed credentials or any number of other anomalies. GuardDuty tracks the following data sources: VPC Flow logs, AWS CloudTrail event logs and DNS logs. AWS charges for the quantity of logs analyzed.
Amazon Inspector. This is a security assessment tool for applications that run on EC2. You activate the tool in the AWS Management Console or install a predefined software agent to run alongside your instances. The tool assesses for vulnerabilities and deviations from AWS security best practices and sends you a list of its findings. You are charged for each instance assessment but the rate decreases the more you use the tool.
Amazon Detective. An IT team would use this investigative service to look for the root cause of security issues or suspicious activity in an AWS environment. Detective ingests time-stamped data from AWS CloudTrail and VPC Flow Logs, as well as GuardDuty findings. It then graphs a complete account of how resources have behaved over time. This information can be used to isolate suspicious activities, such as failed login attempts or questionable API calls.
AWS Security Hub. This AWS security tool provides an overall view of your security posture. It consolidates and prioritizes the data from your AWS accounts to monitor trends and potential issues. It pulls in findings from native security services, such as Amazon GuardDuty and Macie, and integrates with AWS partner products. Security Hub runs its own configuration checks on your resources, comparing your posture against industry standards, such as Center for Internet Security best practices. You are charged for these security checks and the insights you ingest from other security services.
Infrastructure protection
AWS Web Application Firewall (WAF). With this firewall service, you can set conditions to dictate responses to HTTP(S) requests made to Amazon CloudFront, an Amazon API Gateway API or Application Load Balancer. You do this by setting up web access control lists (ACLs) and rules that define the type of requests to allow. For example, you can use AWS WAF to block or allow requests from a certain country. Effectively, you can set these three WAF functions:
- Allow all requests except the ones you specify; e.g., for a public website.
- Block all requests except the ones you specify; e.g., for a restricted website.
- Track the requests that match the conditions you specify; e.g., to workshop your restrictions.
You're charged for the number of web ACLs and rules per web ACL you create, along with the number of requests you receive.
AWS Shield. This is a managed distributed denial of service (DDoS) protection service. Shield is available as a free standard service, which protects against common DDoS attacks. There's also an advanced version users pay for. The advanced version adds DDoS protection for AWS instances, load balancers, CloudFront distributions, Amazon Route 53 hosted zones and AWS Global Accelerators.
AWS Firewall Manager. This tool centralizes AWS WAF and Shield management across all your accounts and resources. Firewall Manager automates firewall protections and settings as you create new resources and accounts. It's useful when setting up infrastructure protection across an entire organization.
Data protection
AWS Key Management Service (KMS). Use this managed service to create and manage cryptographic keys. AWS KMS integrates with most Amazon cloud services, so you can use these keys to encrypt your data across your AWS environment. You can also use an integration with AWS CloudTrail to monitor when and how your keys have been used. Each master key you create in KMS costs $1 per month until it's deleted.
AWS Secrets Manager. This tool controls so-called secrets, such as database credentials, passwords or API keys that are required to access AWS applications. AWS Secrets Manager enables you to automate the rotation of secrets and to programmatically replace credentials in your code, instead of having to manually update secrets within an application. This saves time and maintains compliance. Secrets Manager charges you per secret per month and per 10,000 API calls.
Amazon Macie. This service deploys machine learning to identify and secure sensitive data in S3 buckets. Set up Macie to continually monitor your buckets, so you can track and secure data as it enters your infrastructure. From there, you can view the Macie dashboard to monitor business-sensitive data and set up alerts for incident response. You can also use the service programmatically with AWS SDKs and command-line interfaces. You're charged for the number of S3 buckets evaluated and the amount of data processed.
AWS Certificate Manager. This service handles the management of Secure Sockets Layer/Transport Layer Security (SSL/TLS) certificates for your applications on AWS. This resolves the manual task of buying and renewing SSL/TSL certificates to maintain compliance and network security. You request or import a certificate through the Certificate Manger console.
AWS CloudHSM. With this service, you create hardware security modules (HSM) that run cryptographic operations and store cryptographic keys. You can sync and combine multiple modules into a single HSM cluster. You can then generate and manage cryptographic keys, use algorithms to encrypt and decrypt data and more. Another CloudHSM benefit is only you -- not AWS -- have access and control of the keys you create.
Organizations use these features to satisfy compliance demand for data security. However, you might want to stick with AWS KMS if you're looking for a completely managed encryption experience. With CloudHSM, you pay an hourly fee for each HSM you run.








