Amazon Cognito
Amazon Cognito is an Amazon Web Services product that controls user authentication and access for mobile applications on internet-connected devices. The service saves and synchronizes end-user data, which enables an application developer to focus on writing code instead of building and managing the back-end infrastructure. This can accelerate the mobile application development process.
Access control via authentication and authorization requires confirming two things: the identity of the person trying to access the device or website, and if they are actually allowed to do so. Both aspects are critical in ensuring that organizations can keep their networks and protected resources secure from bad actors. Here is where Amazon Cognito comes in.
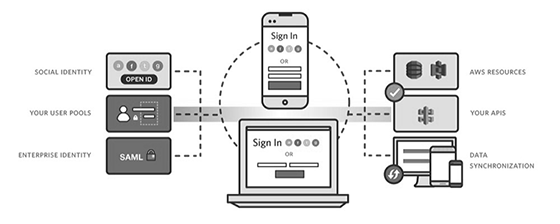
Amazon Cognito collects a user's profile attributes into directories called user pools that a mobile app or web app uses to configure limited access to AWS resources. An identity pool consolidates end-user information, which client access platforms, devices and operating systems receive to organize federated identity groups.
Data synchronizes with AWS when a device is online, allowing an end user to access the same information on another device. Data can also be saved locally to a SQLite database while offline before reconnecting. Amazon Cognito associates data sets with identities and saves encrypted information as key or value pairs in the Amazon Cognito Sync store. Each user can save a maximum of 20 MB of data, with each individual data set containing up to 1 MB.
A developer can configure Amazon Cognito to accept streams of events as data is updated and synchronized. A mobile developer can also query data through other AWS cloud services, such as an Amazon RedShift database, Relational Database Service (RDS) instance or an Amazon Simple Storage Service (S3) file.
What is Amazon Cognito used for?
Amazon Cognito enables simple, secure user authentication, authorization and user management for web and mobile apps. With Cognito, a user or visitor can sign in with a username and password through Amazon, or through a third party like Facebook, Google or Apple.
Thus, with Cognito, a developer can:
- Easily add user sign-up, sign-in and access control to their apps with its built-in user interface (UI) and easy configuration
- Federate identities from social identity providers
- Synchronize data across multiple devices and applications
- Provide secure access to other AWS services from their app by defining roles and mapping users to different roles
Since Cognito handles all authentication requirements, developers can focus on creating apps and websites. This can accelerate the development process, shorten the release cycle, and speed up time to market and time to value.
Cognito is part of the Amazon Web Services (AWS) ecosystem. The Cognito console itself is part of an organization's AWS Management Console, where they can see all information about their Cognito account and billing.
User pools vs. identity pools: Understanding the differences
The two main components of Amazon Cognito are:
- User pools: User directories that provide sign-up and sign-in options for app users.
- Identity pools: Cognito elements grant users access to other AWS services (e.g., Amazon S3 and DynamoDB).
With a user pool, users can sign in to an app through Amazon Cognito, social identity providers (e.g., Google or Facebook), or through Security Assertion Markup Language (SAML) identity providers. Each user will have a directory profile. A developer can access these profiles through a software development kit (SDK). User pools can check for compromised credentials, provide email- and phone-based verification, and offer multifactor authentication (MFA) for additional security. An admin can also integrate AWS Lambda with Amazon Cognito Identity to add logic for customizable security features.
If an organization needs to provide users with access to AWS resources, they can configure an identity pool. Identity pools are federated identities that support authentication through user pools and federated identity providers, SAML identity providers and even unauthenticated identities (guest users). With identity pools, organizations can create unique identities and assign user permissions.
Identity pools and user pools can be used separately or together.
SDK support
A mobile app developer can use a SDK to integrate with Cognito or directly access server-side APIs. AWS supports Amazon Cognito in its AWS Mobile SDK, which includes libraries, code samples and APIs to help developers use the service. The SDK is available for iOS, Android, Unity and Kindle Fire. The AWS SDK for JavaScript also supports Cognito. User pools are available in the AWS SDK for JavaScript and the AWS Mobile SDK for iOS and Android.
How Amazon Cognito authentication works: A 4-step process
Here is how authentication works when identity pools and user pools are used together:
- User signs in through a user pool.
- Once successfully authenticated, they receive a user pool token.
- The app exchanges the token for AWS credentials through an identity pool.
- User can use these authenticated AWS credentials to access other services in the AWS cloud.
Synchronizing user data with AWS Cognito Sync
AWS Cognito Sync synchronizes user profile data across mobile devices and web applications. The feature allows users to obtain a normalized user ID and credentials with Amazon Cognito.
The service supports both Android and iOS devices with high-level client libraries that cache user data locally. The latter makes data available even if a device itself is offline.
User data is persisted in a data set. This data is accessible only to the credentials assigned to a particular identity. To provide user identities, Cognito Sync requires an Amazon Cognito identity pool.
Therefore, to use Amazon Cognito Sync, an organization needs to first set up an identity pool.
Amazon Cognito Security and data protection
Security in Amazon Cognito aligns with the AWS "shared security" model for data protection. AWS provides security of the cloud, while organizations are responsible for security in the cloud.
For an additional layer of security, Amazon Cognito supports MFA and encrypts data at rest and in transit per industry standards. It is also compliant with numerous data protection standards and regulations, including:
Amazon Cognito also supports a number of identity and access management (IAM) capabilities, including:
- Identity-based policies
- Policy actions
- Temporary credentials
- Service roles
- Service-linked roles
Amazon Cognito pricing
Monthly active users (MAUs) determine pricing for Amazon Cognito. A user is an MAU if there is a sign-up, sign-in, token refresh, or password change operation related to that user within a calendar month.
The first 50,000 MAUs are free. Thereafter, the pricing is based on a tiered model based on the number of MAUs.
Charges for Cognito Sync are based on the number of synchronization operations and the amount of data in the Cognito sync store. With the AWS free tier, an enterprise can store 10 GB of data and perform 1,000,000 sync operations in a month, for up to 12 months. Once the free tier is exhausted, Amazon Cognito charges 15 cents per GB of sync storage per month, and 15 cents for every 10,000 sync operations.







