
momius - Fotolia
When should you use AWS IAM roles vs. users?
Access management is critical to securing the cloud. Understand the differences between AWS IAM roles and users to properly restrict access to AWS resources.
Security vulnerabilities can crop up anywhere in the cloud, even in connections to trusted resources and personnel.
However, assigned roles, users and groups help control who has access to what. With the AWS Identity and Access Management (IAM) service, administrators can define access to in-house and outside users, services and applications. Learn more about how AWS IAM roles and users differ, as well how to create them.
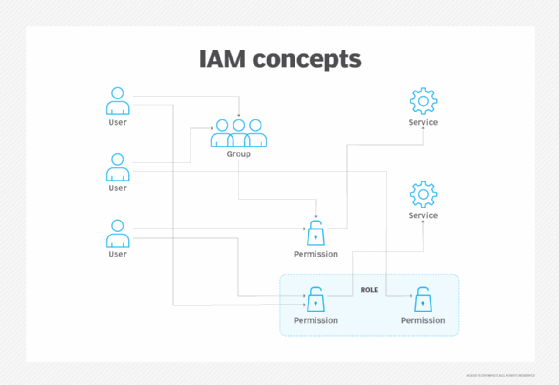
AWS IAM role
An AWS IAM role is an identity within an account that has specific permissions which dictate what the identity can and can't do. Roles help protect resources by dynamically creating access keys to grant temporary access to an account. Admins must apply roles to users, workloads or services that have credentials for AWS access.
Typically, IT teams use AWS IAM roles with applications to handle credentials that run on AWS tools. Admins apply roles to instances so workloads can make secure API requests -- without any concern for underlying security credentials. Also, IAM roles enables admins and developers to delegate API permissions. For example, AWS IAM roles can permit EC2 applications to access storage in S3.
While it's possible to provision and update AWS credentials to each instance -- which allows workloads to sign requests for authentication -- the dynamic environment of a public cloud complicates that process.
To create a role through the IAM console, IAM APIs or AWS Command Line Interface (CLI), admins should follow these steps:
- Define the AWS accounts or service that will take on the defined role, as well as the API actions and resources that the role can access.
- Provision the role as the instance launches. In some cases, admins need to restart instances for the role to take effect.
- Allow the entity -- service, user or API -- that receives the role to retrieve temporary credentials for access.
Consider MFA and identity federation
To further protect identities and access, consider adding extra layers of protection. MFA enhances security for an organization's AWS account and resources. Admins combine username and password details with a unique authentication code the MFA device produces. Admins enable MFA at the AWS account level for individual IAM users within the account and for access to AWS APIs.
Identity federation assigns trust and managed access to outside resources. When a business opens an AWS account and uses IAM, an admin typically creates IAM users and assigns permissions and credentials that allow those users to access resources. Only users or services with IAM credentials and permissions can access resources within a company's AWS account. Federated end users receive permissions or roles and use temporary security credentials to access the AWS Management Console and APIs.
AWS IAM user
An IAM user is an entity that represents a person or application that interacts with AWS. It has specific credentials and permissions attached to it, like roles, to control access. A user is made up of a name, password for the AWS Management Console and access keys to use with the API or CLI. Unlike roles, users are associated with long-term credentials. An IT pro typically chooses to be an IAM user when they create an AWS account and they are the only one that uses it.
For easier management, admins can create user groups, which are a collection of users that share the same permissions. If a new user is added to the user group, that user is automatically given the same permissions of the group. If a user changes jobs in the organization, admins can simply remove them from the group instead of editing their permissions.
To create a user, the core steps include the following:
- Create the user in the AWS Management Console, AWS CLI, AWS API or Tools for Windows PowerShell.
- Create credentials for the user. These credentials are dependent on the type of access the user needs: programmatic access or AWS Management Console access.
- Assign the user to a user group and manage permissions through policies. However, admins can attach permissions policies to just the user.
- Give the user sign-in information.








