hardware security module (HSM)
What is a hardware security module (HSM)?
A hardware security module (HSM) is a physical device that provides extra security for sensitive data. This type of device is used to provision cryptographic keys for critical functions such as encryption, decryption and authentication for the use of applications, identities and databases.
These devices can be plugin cards or be embedded in other hardware, including smart cards, appliances and other external devices. They can be connected to a network server or used as a standalone device offline. They are also offered as cloud services.
Businesses use HSMs to keep cryptographic functions related to transactions, identities and applications separate from regular operations and to control access to those functions. For example, a company might use an HSM to secure trade secrets or intellectual property by ensuring only authorized individuals can access the HSM to complete a cryptography key transfer.
How do HSMs work?
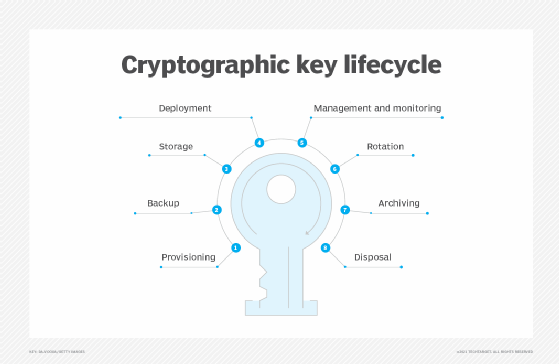
Securing the keys in a cryptographic system is critical to maintaining a secure system. However, managing the lifecycle of those keys is a challenge. And that's where HSMs come in. They manage all aspects of a cryptography key's lifecycle, including the following six steps:
- Provisioning. Keys are created by an HSM, another type of key management system or a third-party organization that does this. A true random number generator should be used to create keys.
- Backup and storage. A copy of a keys should be made and securely stored, in case the key is compromised or lost. They can be stored in the HSM or on external media. Private keys must be encrypted before being stored.
- Deployment. This involves installing the key in a cryptographic device such as an HSM.
- Management. Keys are controlled and monitored based on industry standards and an organization's own internal policies. The encryption key management system handles key rotation where new keys are deployed as existing keys expire.
- Archiving. Decommissioned keys are put in offline, long-term storage for when they may be needed to access existing data that was encrypted with that key.
- Disposal. Keys should be securely and permanently destroyed only after it is determined that they are no longer needed.
The hardware security module protects cryptographic keys and handles the encryption and decryption processes.
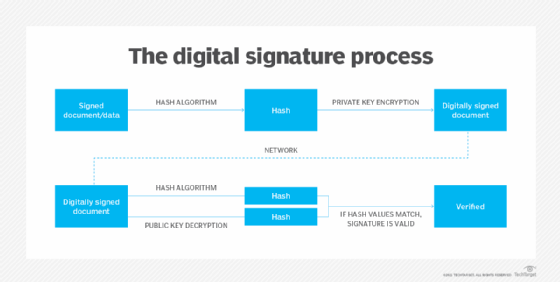
HSMs also can create and verify digital signatures. All access transactions involving an HSM are logged to create an audit trail. The devices enable businesses to move sensitive information and processes from paper documentation to a digital format. Multiple HSMs can be used together to deliver public key management and minimize impact on an application's speed.
Important HSM features
The following are hardware security module features that contribute to their security:
- Secure design. HSMs use specially designed hardware that adheres to government standards such as Federal Information Processing Standardization (FIPS) 140-2, Common Criteria and the HSM requirements of the Payment Card Industry (PCI).
- Tamper resistant. HSMs undergo a hardening process to make them resistant to illicit tampering and unintentional damage.
- Secure operating system. They have a security-focused operating system.
- Isolated. They are located in a secure physical area of the data center to prevent unauthorized access. Some organizations opt to store their HSMs in a third-party data center, rather than keeping them on site.
- Access controls. HSMs control access to the devices and the data they protect. They are designed to show signs of tampering; some HSMs become inoperable or delete cryptographic keys if tampering is detected.
- APIs. HSMs support a range of application programming interfaces (APIs) that enable application integration and the development of custom applications, including the Public-Key Cryptography Standard and Cryptography API Next Generation.
How are HSMs used?
Any business that handles valuable or sensitive information should consider using a hardware security module. That type of information includes credit or debit card data, intellectual property, customer data and employee information.
HSMs secure data generated by a range of applications, including the following:
- websites
- banking
- mobile payments
- cryptocurrencies
- smart meters
- medical devices
- identity cards and personal identification numbers (PINs)
- digital documents
These devices are also used for several purposes, including digital signing, key generation and management, ensuring compliance, simplifying audits, and securing data and digital identities.
The PCI uses specialized HSMs that provide the added security features required for financial transactions. The applications these devices support include PIN management; provision of payment card and mobile app credentials; and verification capabilities for PINs, payment cards and other functions.
Cloud computing and HSMs
The advent of cloud computing has complicated the process of securing sensitive data, as more of it has moved to the cloud. On-premises HSM devices cannot always be used in cloud environments. Cloud service providers can require customers to use HSMs hosted in their data centers. If a provider allows the use a device on premises, connectivity issues can introduce unwanted latency into the system.
Cloud vendors initially provided their own key management services. However, those weren't always usable across hybrid cloud and multi-cloud environments. Customers were left having to deal with the complexities of multiple key management tools to accommodate their hybrid and multi-cloud strategies.
Key management as a service (KMaaS) has emerged as a way to secure encryption keys across different cloud environments. These services offer centralized, on-demand HSM-level tools without the need to provision hardware. As a business expands and diversifies the cloud services it uses, it can turn to the same KMaaS to deploy and manage the encryption keys it needs across various cloud vendors' services.
KMaaS products adhere to the same standards as on-premises HSMs and support a variety of APIs. With these systems, encryption key management functions take place at a digital edge node, minimizing latency and improving application performance.
AWS, Google, IBM and Microsoft all offer cloud KMaaS products, along with smaller companies such as Entrust and Thales.
Data security and privacy compliance
Hardware security modules are at the center of data security and privacy issues. Because of this, they are under increased scrutiny, as business and other organizations face increasing threats in these areas. More specialized HSMs must comply with a range of standards and regulations, including the following:
- European Union's General Data Protection Regulation;
- PCI Data Security Standard;
- Domain Name System Security Extentions;
- FIPS 140-2; and
- Common Criteria.
The takeaway
Hardware security modules are a central piece of data security in the enterprise. They provide the centralized key generation, management and storage businesses need, as well as authentication and digital signing capabilities. HSM technology has proven to have the flexibility needed to keep up with the move to the cloud and the increasing threat environment organizations face today.
Learn more about all aspects of data protection and compliance in our comprehensive guide to data security.






